smm50
Installed anti-virus software (Clam AntiVirus).
Install Clam AntiVirus.
[root@www ~]# 50_1dnf -y install clamav clamav-update
s51Configure Clam AntiVirus.
[root@www ~]# 51_1vi /etc/freshclam.conf
s52Line 8: Add “#” at the beginning of the line to make it a comment.
52_1#Example
s53Update pattern files.
[root@www ~]# 53_1freshclam ClamAV update process started at Sun Jun 30 23:51:01 2019 main.cvd is up to date (version: 58, sigs: 4566249, f-level: 60, builder: sigmgr) daily.cld is up to date (version: 25496, sigs: 1606212, f-level: 63, builder: raynman) bytecode.cvd is up to date (version: 328, sigs: 94, f-level: 63, builder: neo)
s54Run a scan to make sure it works.
[root@www ~]# 54_1clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 6163086 Engine version: 0.101.2 Scanned directories: 38 Scanned files: 23 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 179.738 sec (2 m 59 s)
s55Download a test harmless virus.
[root@www ~]# 55_1wget http://www.eicar.org/download/eicar.com
s56Run a scan to make sure it works.
[root@www ~]# 56_1clamscan --infected --remove --recursive . ----------- SCAN SUMMARY ----------- Known viruses: 6163097 Engine version: 0.101.2 Scanned directories: 3 Scanned files: 10 Infected files: 1 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 179.738 sec (2 m 59 s)
s57
Introduced a file tampering detection system (Tripwire).
Install Tripwire.
[root@www ~]# 57_1dnf -y install tripwire
s58Initialize Tripwire.
[root@www ~]# 58_1tripwire-setup-keyfiles
s59Set a passphrase for the site key file.
Enter the site keyfile passphrase: Site key file passphrase (alphanumeric) Verify the site keyfile passphrase: Site key file passphrase (alphanumeric)
s60Sets the passphrase for the local keyfile.
Enter the local keyfile passphrase: Local key file passphrase (alphanumeric) Verify the local keyfile passphrase: Local key file passphrase (alphanumeric)
s61Enter the passphrase for the site key file.
Please enter your site passphrase: Site key file passphrase
s62Enter the passphrase for the site key file.
Please enter your site passphrase: Site key file passphrase
s63Change the directory to “/etc/tripwire”.
[root@www ~]# 63_1cd /etc/tripwire
s64Make initial settings.
[root@www tripwire]# 64_1vi twcfg.txt
s65Line 12: Change the reporting level to maximum.
REPORTLEVEL = 65_14
s66Generate a configuration file.
[root@www tripwire]# 66_1twadmin -m F -c tw.cfg -S site.key twcfg.txt
s67Enter the passphrase for the site key file.
Please enter your site passphrase: Site key file passphrase
Wrote configuration file: /etc/tripwire/tw.cfg
s68Optimize your policy.
[root@www tripwire]# 68_1vi twpolmake.pl
s69If “#” is automatically inserted at the beginning of the line, create it in two steps.
69_1#!/usr/bin/perl 69_2# Tripwire Policy File customize tool # ---------------------------------------------------------------- # Copyright (C) 2003 Hiroaki Izumi # This program is free software; you can redistribute it and/or # modify it under the terms of the GNU General Public License # as published by the Free Software Foundation; either version 2 # of the License, or (at your option) any later version. # This program is distributed in the hope that it will be useful, # but WITHOUT ANY WARRANTY; without even the implied warranty of # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the # GNU General Public License for more details. # You should have received a copy of the GNU General Public License # along with this program; if not, write to the Free Software # Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA. # ---------------------------------------------------------------- # Usage: # perl twpolmake.pl {Pol file} # ---------------------------------------------------------------- # #Create a line without "#" at the beginning of the line, and do the following. 69_3$POLFILE=$ARGV[0]; open(POL,"$POLFILE") or die "open error: $POLFILE" ; my($myhost,$thost) ; my($sharp,$tpath,$cond) ; my($INRULE) = 0 ; while (<POL>) { chomp; if (($thost) = /^HOSTNAMEs*=s*(.*)s*;/) { $myhost = `hostname` ; chomp($myhost) ; if ($thost ne $myhost) { $_="HOSTNAME="$myhost";" ; } } elsif ( /^{/ ) { $INRULE=1 ; } elsif ( /^}/ ) { $INRULE=0 ; } elsif ($INRULE == 1 and ($sharp,$tpath,$cond) = /^(s*#?s*)(/S+)b(s+->s+.+)$/) { $ret = ($sharp =~ s/#//g) ; if ($tpath eq '/sbin/e2fsadm' ) { $cond =~ s/;s+(tune2fs.*)$/; #$1/ ; } if (! -s $tpath) { $_ = "$sharp#$tpath$cond" if ($ret == 0) ; } else { $_ = "$sharp$tpath$cond" ; } } print "$_n" ; } close(POL) ; [root@www tripwire]# 69_4perl twpolmake.pl twpol.txt > twpol.txt.new [root@www tripwire]# 69_5twadmin -m P -c tw.cfg -p tw.pol -S site.key twpol.txt.new
s71Enter the passphrase for the site key file.
Please enter your site passphrase: Passphrase for your site key file
Wrote configuration file: /etc/tripwire/tw.pol
s72Create a database.
[root@www tripwire]# 72_1tripwire -m i -s -c tw.cfg
s73Enter the passphrase for the local key file.
Please enter your local passphrase: Local key file passphrase
s74Move directory.
[root@www tripwire]# 74_1cd
s75Run the check. (Regular checks are performed daily.)
[root@www ~]# 75_1tripwire -m c -s -c /etc/tripwire/tw.cfg Open Source Tripwire(R) 2.4.2.2 Integrity Check Report Report generated by: root ... ... ... All rights reserved.
s76Confirm the check result.
[root@www ~]# 76_1ll /var/lib/tripwire/report total 4 -rw-r--r-- 1 root root 1821526 6月 29 07:58 server.jp-20190629-075230.twr -rw-r--r-- 1 root root 1830182 6月 30 06:09 server.jp-20190630-060029.twr -rw-r--r-- 1 root root 1829590 7月 1 09:29 server.jp-20190701-092314.twr -rw-r--r-- 1 root root 1828518 7月 1 17:27 server.jp-20190701-171400.twr
s77Specifies a report to update the database.
[root@www ~]# 77_1tripwire -m u -a -s -c /etc/tripwire/tw.cfg -r /var/lib/tripwire/report/server.jp-20190701-171400.twr
s78Enter the passphrase for the local key file.
Please enter your local passphrase: Local key file passphrase
s79
Rootkit detection system introduced (RkHunter).
Install RKHunter.
[root@www ~]# 79_1dnf -y install rkhunter
s80Set up RKHunter.
[root@www ~]# 80_1vi /etc/sysconfig/rkhunter
s81Set the destination to send the report and scan mode.
81_1#Destination to send the report to
MAILTO=root@localhost
#Scan mode
DIAG_SCAN=no
s82Update the database.
[root@www ~]# 82_1rkhunter --update
s83Update system file information.
[root@www ~]# 83_1rkhunter --propupd
s84Run check.
[root@www ~]# 84_1rkhunter --check --sk [ Rootkit Hunter version 1.4.2 ] Checking system commands... ... ... No warnings were found while checking the system.
s85
Settings for SSH server public key authentication method connections.
Create a public key for the server.
Start TeraTerm, log in as a user, and create public and private keys.
[webmaster@www ~]$ 85_1ssh-keygen -t ecdsa
s86Press “Enter”.
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/webmaster/.ssh/id_ecdsa):
s87Set “Passphrase”.
Enter passphrase (empty for no passphrase):Passphrase
Enter same passphrase again:Passphrase
s88Transfer the public key to “.ssh/”.
[webmaster@www ~]$ 88_1mv ~/.ssh/id_ecdsa.pub ~/.ssh/authorized_keys
s89Configure your login settings.
[webmaster@www ~]$ 89_1chmod 700 .ssh/
s90Log in as root and transfer the private key to “/samba/share”.
[root@www ~]# 90_1mv /home/webmaster/.ssh/id_ecdsa /samba/share [root@www ~]# 90_2chmod 777 /samba/share/id_ecdsa
s91Save the “id_ecdsa” file from the Samba shortcut on the client PC to any location (SSH key/private key/).
Connection test.
Select “New Connection”.
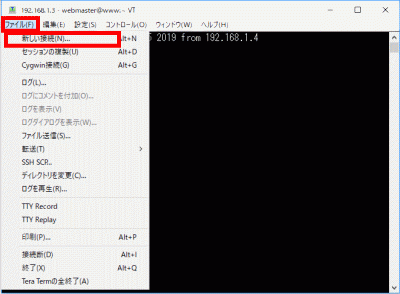
s92Enter the IP address in “Host” and click “OK”.
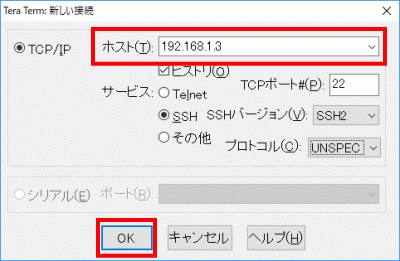
s93Enter “Username” and “Passphrase (key passphrase)”.
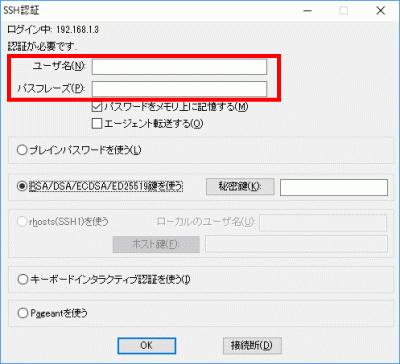
s94Select “Use RSA/DSA/ECDSA/ED25519 key”.
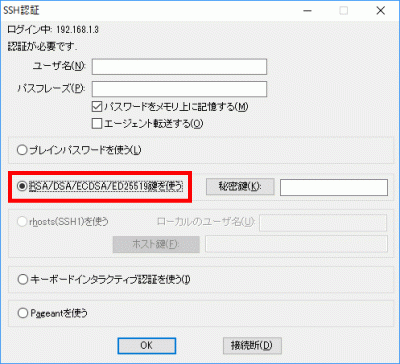
s95Click “Private Key” and select the saved “SSH Key/Private Key/id_ecdsa”.
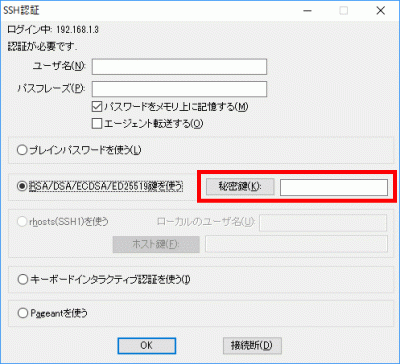
s96Click OK to confirm the connection.
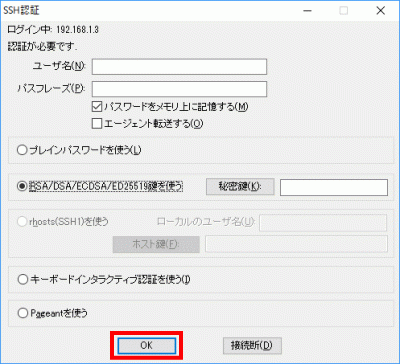
s97Log in to root.
[webmaster@www ~]$ 97_1su - Password:
s98
Authenticated connection with private key.
Create a backup.
[root@www ~]# 98_1cp -p /etc/ssh/sshd_config /etc/ssh/sshd_config_bck
s99Edit.
[root@www ~]# 99_1vi /etc/ssh/sshd_config
s100Line 65: Change “yes” to “no”.
PasswordAuthentication 100_1no
s101Restart SSH.
[root@www ~]# 101_1systemctl restart sshd



コメント